Ingest SBOM from Snyk into SSCA
This workflow describes how to ingest Snyk scan results into a Harness pipeline. STO supports the following scan approaches for the following Snyk products:
- Snyk Container SBOM via an ingestion workflow
- Snyk Open Source SBOM via STO Snyk step
Generating and ingesting a Snyk Container SBOM
A Software Bill of Materials (SBOM) is a list of all the components, libraries, and other dependencies used in a software application. Harness SSCA can ingest JSON SPDX or CycloneDx formatted SBOM from any tool that can generate these report formats.
Generate a key pair
Keys are used to sign and verify attestations.
- Generate a public and private key pair. For example, you can use Cosign to generate key pairs.
- Create two Harness file secrets, one for the private key file and one for the public key file.
- Create a Harness text secret to store the password for the private key.
Configure your pipeline to ingest SBOM
In your Harness pipeline, go to the stage where you want to ingest the SBOM, and select the Overview tab.
In Shared Paths, enter a path to a location where your SBOM can be stored on the build machine, such as
/shared/customer_artifacts.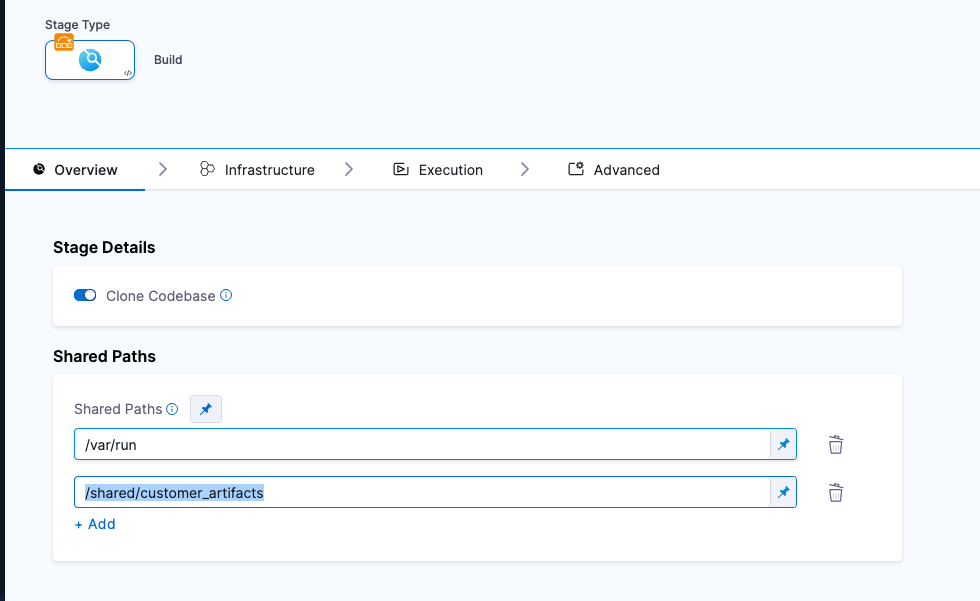
Add a step to your stage that generates an SBOM, such as a Run, Plugin, or GitHub Action step.
For example, you could use the following command in a Run step to generate a Snyk SBOM.
snyk container sbom --format=spdx2.3+json \
ubuntu:22.04 > /shared/customer_artifacts/result.spdx.json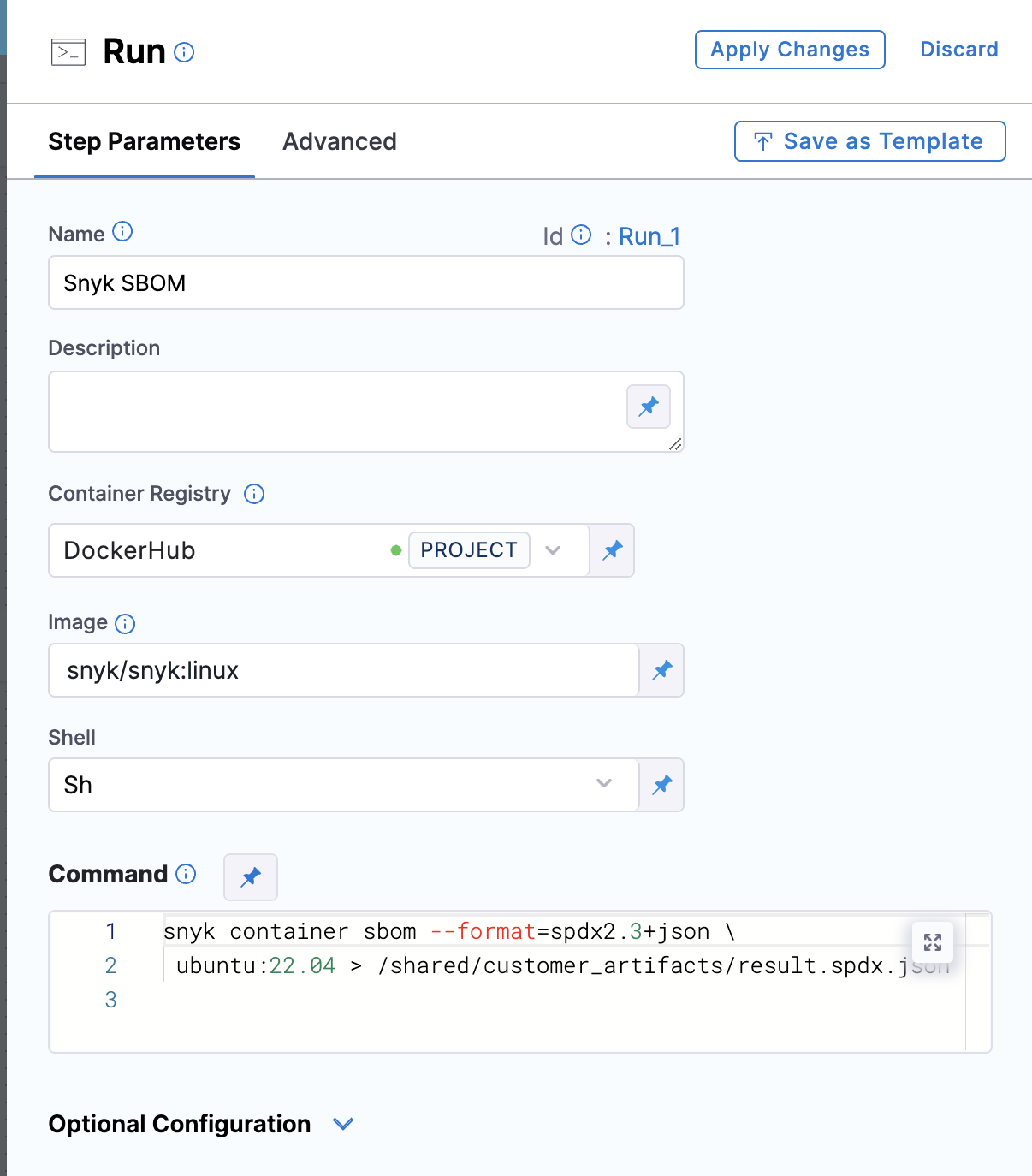
Verify that step above is configured to output the file to one of the Shared Paths (i.e /shared/customer_artifacts/result.spdx.json)
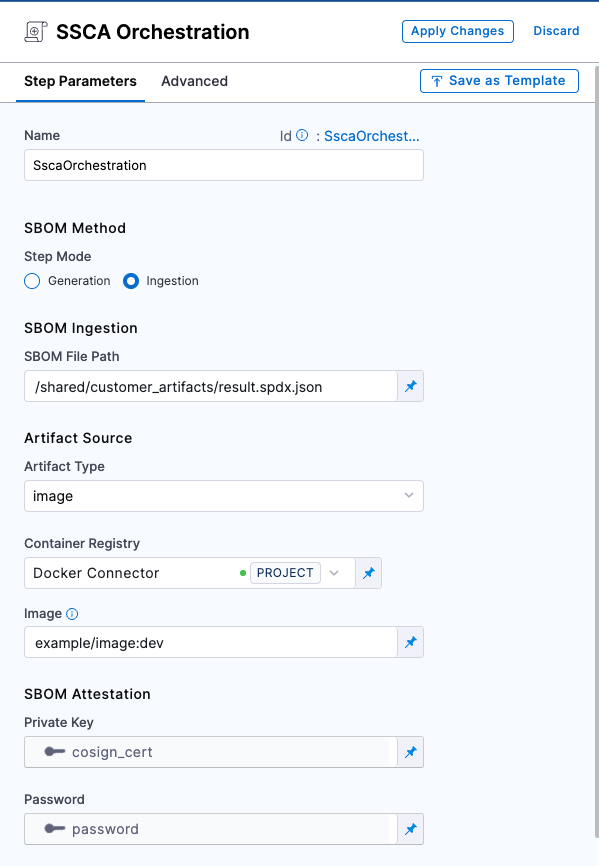
Add an SSCA Orchestration step configured to ingest the SBOM:
- Set the Step Mode to Ingestion.
- For SBOM File Path, enter the path to the SBOM file generated by Snyk Container.
- For Container Registry, select the Docker Registry connector that is configured for the Docker-compliant container registry where you stored the artifact associated with the SBOM, such as Docker Hub, Amazon ECR, or GCR.
- For Image, enter the repo path (in your container registry) and tag for the image associated with the SBOM, such as
my-docker-repo/my-artifact:latest. - Private Key: The Harness file secret containing the private key to use to sign the attestation.
- Password: The Harness text secret containing the password for the private key.
If you're using Docker-compliant ECR or GCR repositories, you must:
- Configure your Docker Registry connector as a valid artifact source.
- For ECR, go to Use Docker Registry for ECR.
- For GCR, go to Use Docker Registry for GCR
- Use the full URI for the Image in your SSCA Orchestration step, such as
1234567890.dkr.ecr.REGION.amazonaws.com/IMAGE_NAME:TAG.
Generate and ingest a Snyk Open Source SBOM
Harness SSCA can ingest SBOM generated from STO scanner steps, such as the Snyk STO step, if the resulting SBOM is in JSON SPDX or CycloneDx format.
This topic explains how to configure a pipeline to ingest SBOM generated by an STO scanner step. It uses the Snyk STO step as an example.
You can also generate SBOM using built-in SBOM tools or ingest SBOM from any SBOM tool.
Generate a key pair
Keys are used to sign and verify attestations.
- Generate a public and private key pair. For example, you can use Cosign to generate key pairs.
- Create two Harness file secrets, one for the private key file and one for the public key file.
- Create a Harness text secret to store the password for the private key.
Configure the STO scan step to generate SBOM
Configure the Snyk STO scanner step, and make sure you select Generate SBOM and the SBOM Format.

Get the SBOM file path
The Snyk STO step creates a JOB_ID output variable that you can use to reference the SBOM file path in the SSCA Orchestration step.
Replace
STAGE_IDandSTEP_IDin the following Harness expression with the stage ID and step ID for your Snyk STO step.<+pipeline.stages.STAGE_ID.spec.execution.steps.STEP_ID.output.outputVariables.JOB_ID>Use the expression in your SBOM file path. The exact path depends on where your scanner outputs SBOM files. For example, this filepath references a Snyk STO step with the ID
mysnykstepin a stage with the IDmybuildstage:/addon/results/<+pipeline.stages.mybuildstage.spec.execution.steps.mysnykstep.output.outputVariables.JOB_ID>.sbom
Alternately, you can get the output path and output variable expression from a previous run of the same pipeline. To do this, go to the execution details page, select the stage with the STO scanner step, and then select the STO scanner step. In the step's logs, you can find the output path, and you can get the output variable from the Output tab.
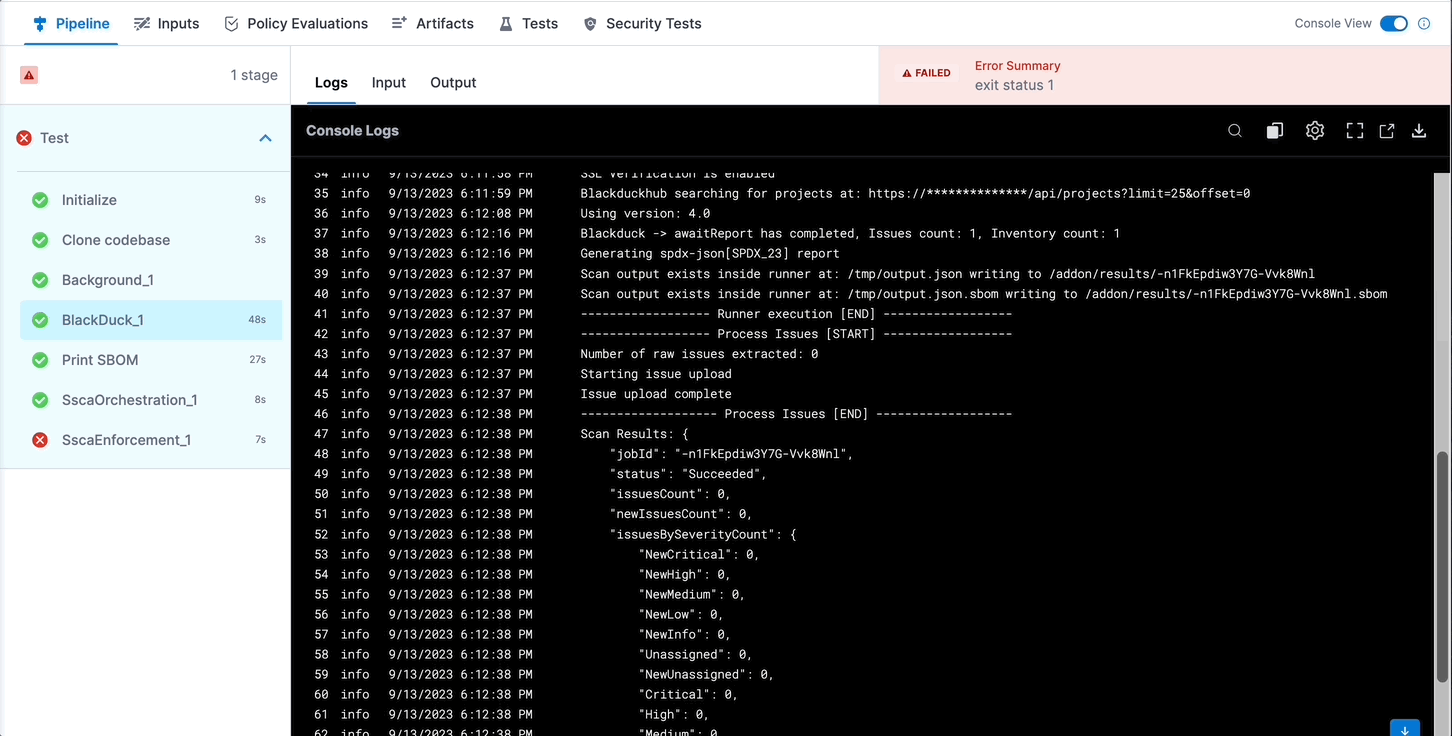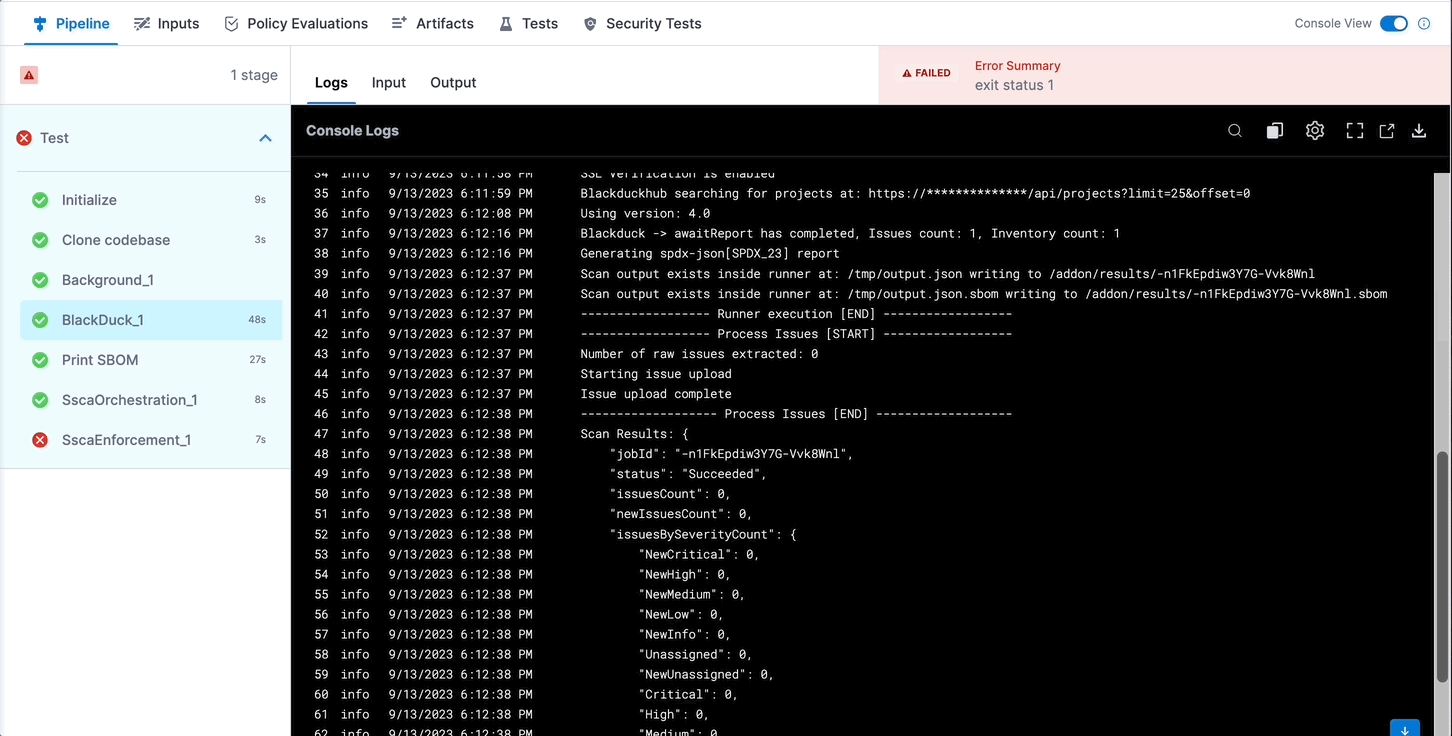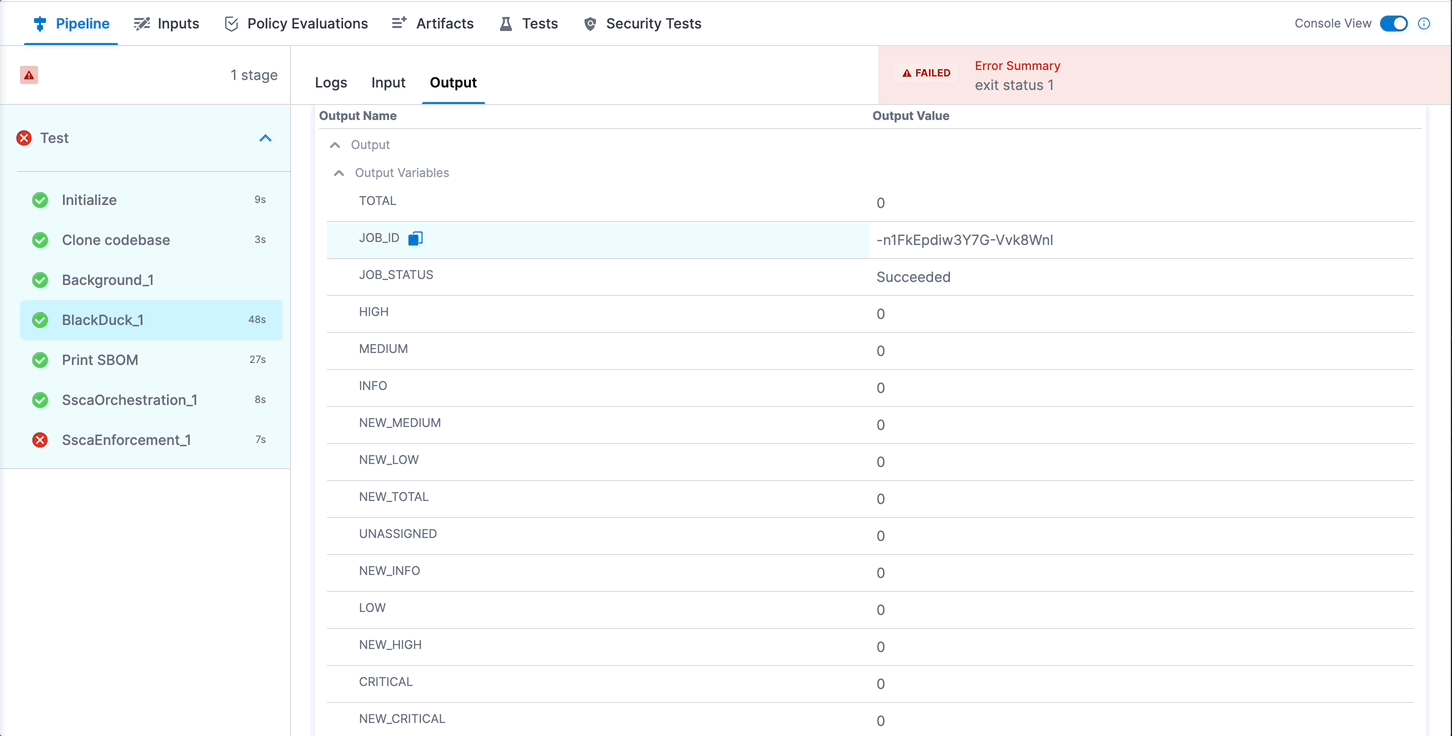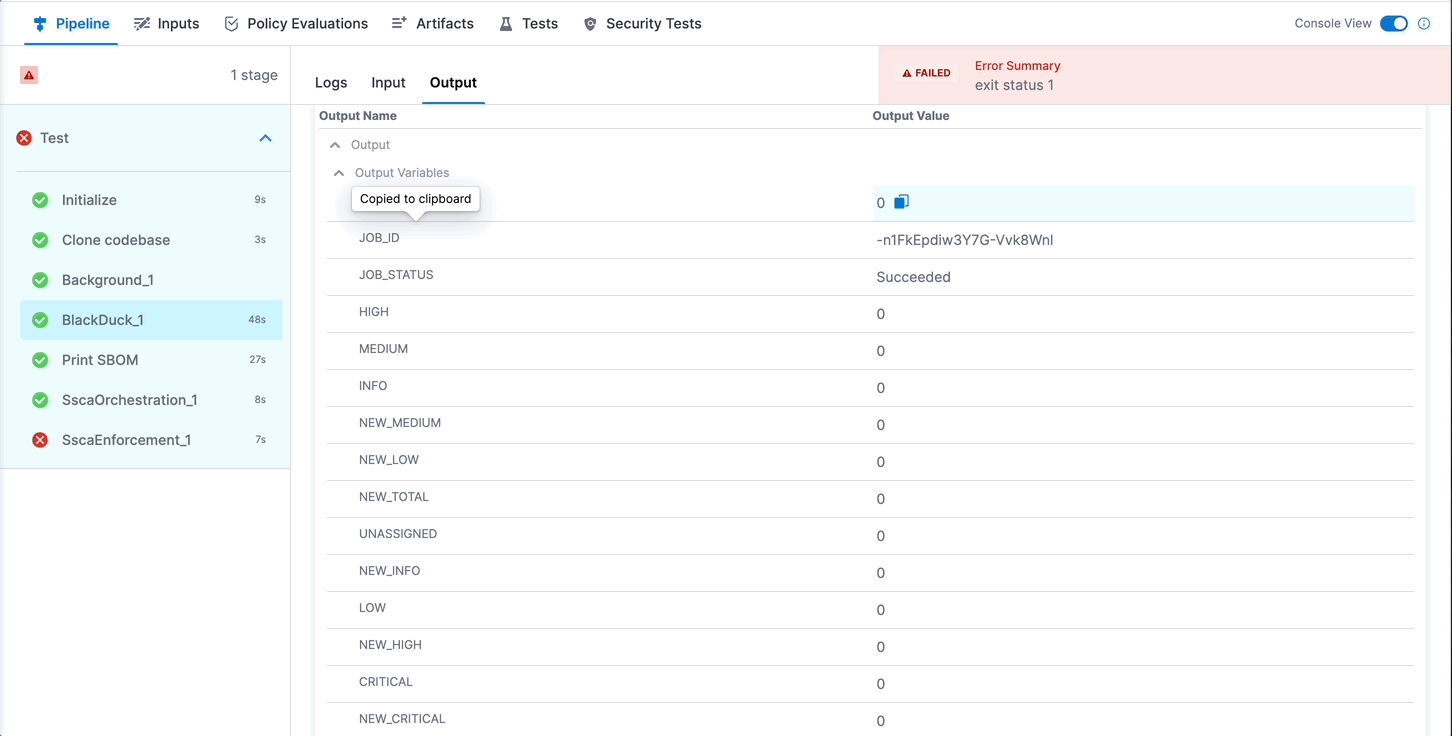
Configure the SSCA Orchestration step
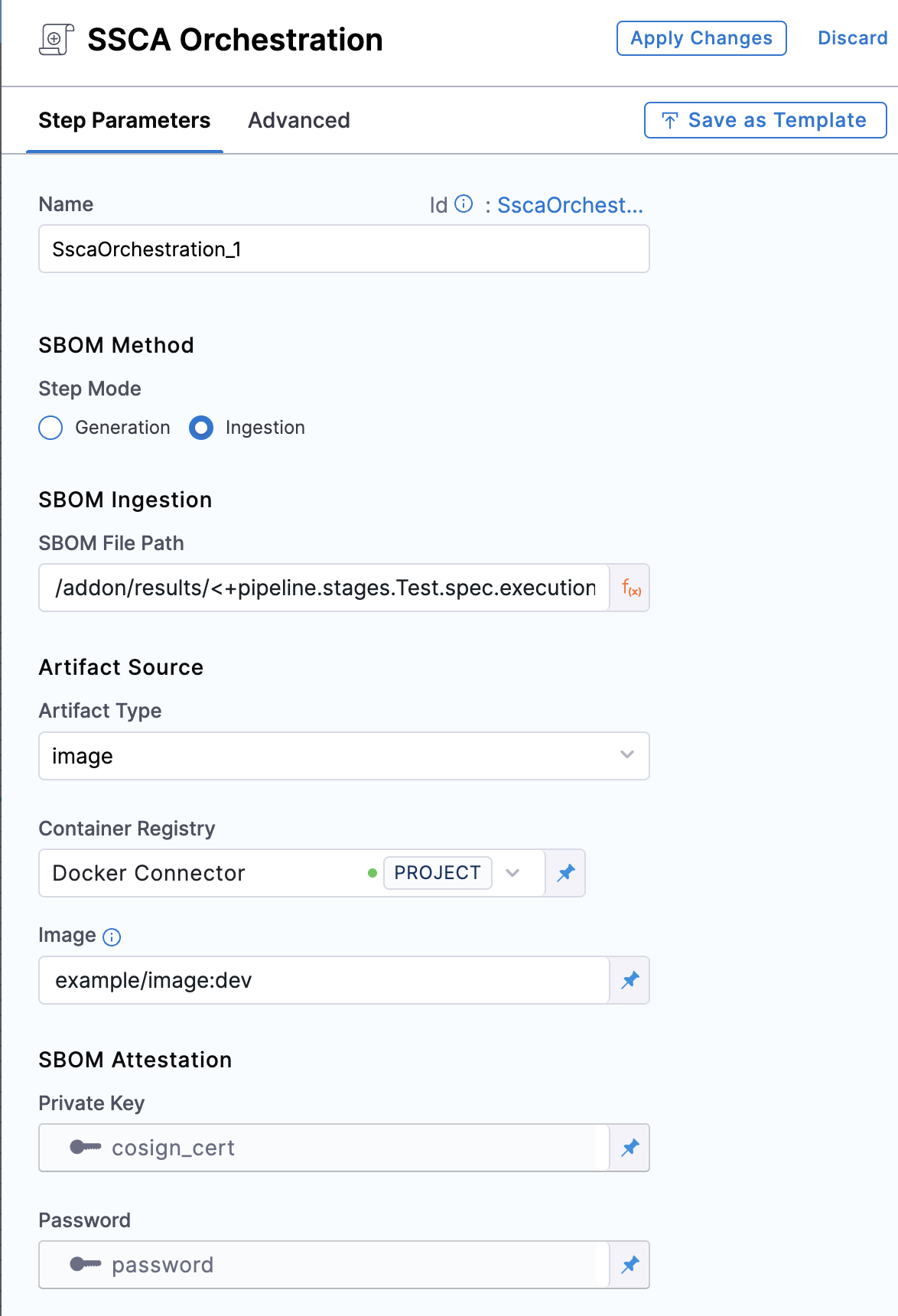
Add an SSCA Orchestration step configured to ingest the SBOM.
- Set the Step Mode to Ingestion.
- For SBOM File Path, enter the SBOM file path that uses the
JOB_IDvalue, as explained in Get the SBOM file path. - For Container Registry, select the Docker Registry connector that is configured for the Docker-compliant container registry where you stored the artifact associated with the SBOM, such as Docker Hub, Amazon ECR, or GCR.
- For Image, enter the repo path (in your container registry) and tag for the image associated with the SBOM, such as
my-docker-repo/my-artifact:latest. - Private Key: The Harness file secret containing the private key to use to sign the attestation.
- Password: The Harness text secret containing the password for the private key.
If you're using Docker-compliant ECR or GCR repositories, you must:
- Configure your Docker Registry connector as a valid artifact source.
- For ECR, go to Use Docker Registry for ECR.
- For GCR, go to Use Docker Registry for GCR
- Use the full URI for the Image in your SSCA Orchestration step, such as
1234567890.dkr.ecr.REGION.amazonaws.com/IMAGE_NAME:TAG.
